It looks like cybercriminals are looking for the “bigger fish in the sea” with the rise of whaling. While phishing middle to lower level employees is still extremely relevant in the world of cybersecurity, some attackers are now looking for a bigger reward by going after the executives. The term “whaling” is more than fitting as it refers to phishing executives (whales) of large corporations.
What is Whaling?
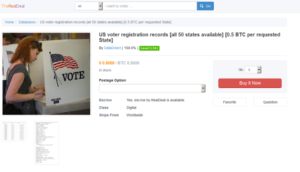
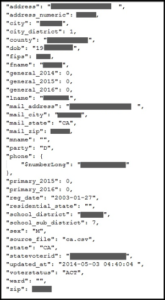
Whaling refers to targeted spear-phishing campaigns directed at senior executives, who often have access to delicate information such as employee or customer data. A successful whaling attack can yield executive passwords and other account details that can open up corporate hard drives, company networks, and even commercial bank accounts.
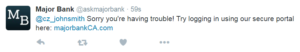
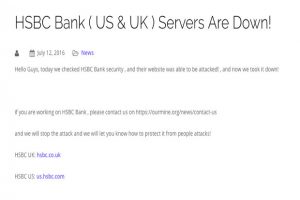
Where a regular phishing email will typically address a personal aspect of the target’s life, a whaling email will likely take the form of a business critical email, customized to a senior executive’s precise position and responsibilities in the company. Last year, a senior executive in charge of customer satisfaction at his company opened an email about a customer complaint. He followed the link to see the details of the complaint only to find himself redirected to an illegitimate website that ended up giving the attacker access to his company’s network.
Going After the Big Catch
In the last two years alone, as many as 7,000 US businesses have fallen victim to whaling attacks, resulting in over $740 million in losses. With the rewards for a successful cyberattack becoming bigger and bigger each day, so too are the security measures corporations are taking. Unfortunately, cybercriminals are also becoming more sophisticated with their attacks. With whaling, however, criminals must become more educated about their targets.
Most senior executives are aware of all the malicious spam they could encounter. Cybercriminals are now taking months to research the company they are after, to find out as much as possible in order to craft an email in a way that seems completely legitimate to the recipient. A successful attack happens only when the cybercriminal sends an email that has a reasonable rationale and builds trust by including pertinent and specific information that seems confidential.
Attackers have even begun to take to social media to see what charities or hobbies their target executive is involved in. Executives with open public profiles make prime targets for whaling attacks.
Don’t Become the Next Trophy Catch
Here are some guidelines to follow to limit your exposure to becoming the next trophy on the wall for cybercriminals:
- Minimize or lock down the exposure of senior management by implementing privacy restrictions
- Facebook – Don’t have an open profile that is visible to the general public and be weary of accepting friend requests from individuals you don’t know
- Twitter/Instagram – Don’t let anyone and everyone follow you. Make sure to implement security measures where you can accept/deny follow requests.
- Don’t rely on traditional security tools to safeguard network user information
- Monitor suspicious emails by creating a reporting system
- Assess your organization’s overall exposure to phishing attacks – launch a practice phishing attack to see how many employees actually visit the website in the email.