
Kaspersky Lab has detected almost four times as many attacks on its Android customers compared to last year
The number of users infected with mobile ransomware is skyrocketing, as hackers try to expand the number of potential victims they can target.
Compared with a year ago, almost four times as many users are being attacked by mobile ransomware, security firm Kaspersky Lab said on Wednesday.
It’s a troubling trend. Ransomware has typically targeted PCs by encrypting all the information that is inside the targeted machines, and then holding the data hostage in exchange for money.
The threat is that users who fail to pay ransom will see all the data erased. Hospitals, schools and police departments have all been major victims. But increasingly, hackers have begun focusing on smartphones.
Kaspersky looked at its own Android customers and noticed the spike. Between April 2015 and March this year,136,532 of its users encountered a mobile version of ransomware. That’s up from 35,413 in the year earlier period.
Kaspersky customers in Germany, Canada, the U.K. and the U.S., in that order, were the top four countries affected by mobile ransomware.
The largest mobile ransomware family detected is called Fusob, Kaspersky said. It was responsible for 56 percent of the attacks during the year and targets Android users.
Victims are unwittingly downloading it when visiting porn sites. Fusob masquerades as a multimedia player, called xxxPlayer, that’s been designed to watch the porn videos.
Once downloaded, Fusob can block all user access to a device. Victims are told to pay between $100 and $200 in iTunes gift cards to deactivate the block.
Most of the victims have been located in Germany. The ransomware ignores devices that use Russian and several Eastern European languages.
Kaspersky noted that much of mobile ransomware detected actually doesn’t encrypt any information on the infected device. Smartphone owners usually back up all their data to a cloud service anyway, so there’s no point to try and encrypt it, the security firm said. Instead, the ransomware blocks user access to apps on the phone. Often, victims of mobile ransomware will see a ransom note on their device’s screen with instructions on how to pay the ransom, and will not be able to use the phone otherwise until they do so.
Hackers are increasingly using mobile malware in order to expand the number of potential targets outside of PCs, according to security firms.
“In the end, they’re going to follow the money, and find what’s most effective,” said Christopher Budd, the communications manager with Trend Micro. He expects ransomware to continue to evolve and possibly target more Android-based devices, including smart TVs in the future.
To avoid ransomware, Kaspersky advises that users regularly update their software and back up all crucial files. Users should also be wary of downloading anything from untrusted sources and look into buying strong security software.
 The newest game craze to sweep the nation is Pokémon GO. The popular game, created by Silicon Valley’s Niantic Labs, uses your phone’s GPS to detect where you are and make the Pokémon characters appear on your phone’s screen. As you move, you encounter more characters. Of course, this is all from second hand as I have chosen not to download and play.
The newest game craze to sweep the nation is Pokémon GO. The popular game, created by Silicon Valley’s Niantic Labs, uses your phone’s GPS to detect where you are and make the Pokémon characters appear on your phone’s screen. As you move, you encounter more characters. Of course, this is all from second hand as I have chosen not to download and play.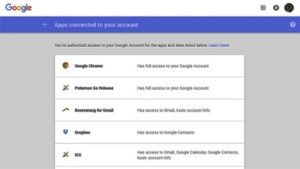 Those who chose to download the game via Google on an iPhone gave the creators at Niantic full and total access to their Google accounts. This allowed the developers access to users’ Google photos, e-mail, browser history, map history and more. Yikes!
Those who chose to download the game via Google on an iPhone gave the creators at Niantic full and total access to their Google accounts. This allowed the developers access to users’ Google photos, e-mail, browser history, map history and more. Yikes!






 were the case, those of us in the cybersecurity industry would be without employment. However, training to reduce the risk of cybercriminal activity is essential to a company’s bottom line. Without training and security measures we may as well leave the front door open at night with a sign stating, “Welcome all criminals.”
were the case, those of us in the cybersecurity industry would be without employment. However, training to reduce the risk of cybercriminal activity is essential to a company’s bottom line. Without training and security measures we may as well leave the front door open at night with a sign stating, “Welcome all criminals.”