Equifax previously disclosed data was potentially accessed in May
Hackers roamed undetected in Equifax Inc.’s computer network for more than four months before its security team uncovered the massive data breach, the security firm FireEye Inc. said this week in a confidential note Equifax sent to some of its customers.
FireEye’s Mandiant group, which has been hired by Equifax to investigate the breach, said the first evidence of hackers’ “interaction” with the company occurred on March 10, according to the Mandiant report, which was reviewed by The Wall Street Journal.
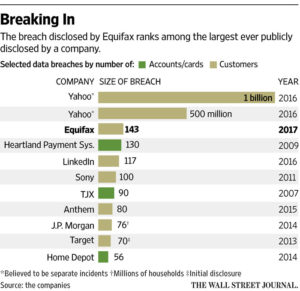
Equifax had previously disclosed that data belonging to approximately 143 million Americans was potentially accessed in May. It isn’t known when Equifax learned from Mandiant that the hacking activity began in March, not May. Equifax wasn’t available for comment.
Equifax has said it didn’t discover the breach until July 29. Days later it called in Mandiant. Equifax didn’t disclose the breach until Sept. 7.
The attack, which is being probed by the Federal Bureau of Investigation, is one of the most significant data breaches given the scope of the information disclosed: people’s names, addresses, dates of birth and Social Security numbers. In its wake, consumers, customers, regulators and legislators have been asking how the attack occurred and whether Equifax took sufficient measures to protect such sensitive information.
Equifax sent the Mandiant report to some customers, many of which are financial firms, with a cover letter dated Tuesday, Sept. 19, that was signed by the company’s new chief information officer, Mark Rohrwasser, and new chief security officer, Russ Ayres. Equifax last Friday announced the departure of the two executives who previously held those positions.
In a progress report that accompanied that announcement last Friday, Equifax said hackers accessed consumers’ data from May 13 through July 30. It didn’t mention in that report that the attack had begun at an earlier date.
Mandiant’s report this week noted the hackers accessed one of Equifax’s servers by taking advantage of a flaw in software called Apache Struts, used by many companies to build interactive websites.
Two days before the access occurred, on March 8, security researchers at Cisco Systems Inc. warned of the flaw in Struts and a patch was issued by the Apache Software Foundation. Equifax in its report last week said its security staff “took efforts” to fix the system, saying it understood the intense focus outside the company on patching efforts and that its review was ongoing.
After interacting with Equifax’s server in early March, the hackers then entered the computer command “Whoami,” Mandiant wrote. This command would have given the attackers the username of the computer account to which they had just gained access, an early step in a hacking attempt.
Investigators have not determined for certain whether the March incident was issued by the data thieves or a different set of hackers, but it was likely the beginning of a monthslong reconnaissance mission, according to a person familiar with the investigation. It is common for attackers to lurk for months after their initial break-in as they probe corporate systems—the digital equivalent of trying as many doorknobs as possible to see which doors can be opened.
The March activity was likely a result of the hackers “spamming the internet for vulnerable systems,” said Johannes Ullrich, dean of research with the SANS Technology Insitute, a cybersecurity training school.
It isn’t surprising that the hackers took weeks before accessing the sensitive data, Mr. Ullrich said. “Typically, you first build out a beachhead so that it’s difficult to get kicked out,” he added.
On average, it takes companies close to 100 days to discover that they have been hacked, FireEye said in a report released earlier this year. In Equifax’s case, it took 141 days.
Eventually, between May 13 and late July, the attackers accessed files that contained Equifax credentials, such as username and password, and “performed database queries that provided access to documents and sensitive information stored in databases in an Equifax legacy environment,” the Mandiant report said.
Overall, the attackers accessed “numerous database tables in several databases,” the Mandiant report said.
The report added that the attackers “compromised two systems” that support Equifax’s online dispute web application. This is the place where consumers go to dispute information on their credit reports.
The hackers also set up about 30 Web shells—hidden pages that would allow them to remotely run commands on Equifax’s systems even if the Struts vulnerability was patched, the report said. The attackers “remotely accessed” the Equifax systems from approximately 35 “distinct public IP addresses,” it added.
The identity of the hackers is still unknown. Mandiant said in its letter that it hadn’t been able to attribute the breach to any “threat group actor” it currently tracks. Nor did the “tools, tactics and procedures” used overlap with those seen in previous investigations by the firm.