The U.S. federal officials have arrested three hackers who have pleaded guilty to computer-crimes charges for creating and distributing Mirai botnet that crippled some of the world’s biggest and most popular websites by launching the massive DDoS attacks last year.
According to the federal court documents unsealed Tuesday, Paras Jha (21-year-old from New Jersey), Josiah White (20-year-old Washington) and Dalton Norman (21-year-old from Louisiana) were indicted by an Alaska court last week on multiple charges for their role in massive cyber attacks conducted using Mirai botnet.
Mirai is a piece of nasty IoT malware that scans for insecure routers, cameras, DVRs, and other Internet of Things devices which are still using their default passwords and then add them into a botnet network, which is then used to launch DDoS attacks on websites and Internet infrastructure.
According to his plea agreement, Jha “conspired to conduct DDoS attacks against websites and web hosting companies located in the United States and abroad” by ensnaring over 300,000 IoT devices. He also demanded payment “in exchange for halting the attack.”
Between September and October 2016, Jha advertised Mirai botnet on multiple dark web forums using the online monikers “Anna Senpai.” He also admitted to securely wiping off the virtual machine used to run Mirai on his device and then posting the source code of Mirai online for free.
Since then, other cybercriminals have used the open-source code of the botnet to create their own Mirai variants in a variety of different cyber attacks against their targets.
Paras Jha (a.k.a Anna Senpai) and his business partner Josiah White (a.k.a Lightspeed and thegenius) are the same people who were outed by blogger Brian Krebs earlier this year after his blog was also knocked offline by a massive 620 Gbps of DDoS attack using Mirai botnet.
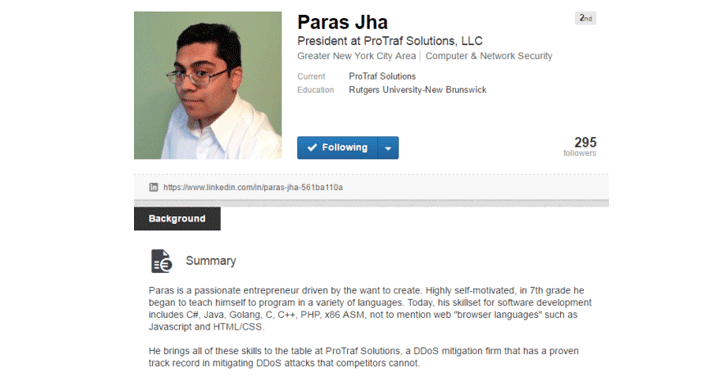
According to Jha’s LinkedIn profile, he is a 21-year-old passionate programmer from Fanwood, U.S., who knows how to code in multiple programming languages and is positioned as president of a DDoS mitigation firm, ProTraf Solutions.
White admitted to creating the Mirai botnet’s scanner to identify and hijack vulnerable internet-connected devices to enlist in the botnet, while Norman (a.k.a Drake) admitted to identifying private zero-day vulnerabilities and exploits to build into the massive botnet.
From December 2016 to February 2017, the trio successfully infected more than 100,000 computing devices to form another powerful botnet, called Clickfraud, which was designed to scam online ad networks by simulating clicks on ads for the purpose of artificially generating revenue.
A week after the massive DDoS attack, the source code of Mirai was released on the widely used hacker chat forum Hackforums by Jha who, under the name Anna-senpai, wrote he had “made their money…so it’s time to GTFO.”
“So today, I have an amazing release for you,” he wrote. “With Mirai, I usually pull max 380k bots from telnet alone. However, after the Kreb [sic] DDoS, ISPs been slowly shutting down and cleaning up their act. Today, max pull is about 300k bots, and dropping.”
Once Mirai source code was out, various cyber criminals started exploiting the IoT malware to launch powerful DDoS attacks against websites and Internet infrastructure, one of which was the popular DNS provider Dyn, which was DDoSed by a botnet of an around 100,000 Mirai malware-infected devices.
“The defendants’ involvement with the original Mirai variant ended in the fall of 2016, when Jha posted the source code for Mirai on a criminal forum. Since then, other criminal actors have used Mirai variants in a variety of other attacks.” DOJ said.
The trio faces a sentence of up to five years in prison.
Crime does not pay, it will eventually catch up to you !!!