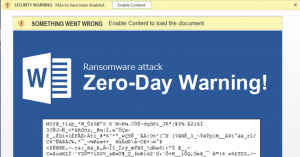
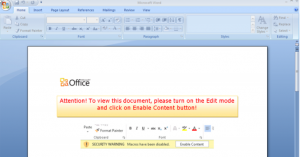
By now, we have all heard about ransomware as it has taken over the cybersecurity scene over the last couple of years. However, we want to make sure that everyone is clear about the difference between cyber ransom and ransomware, as there is a very clear distinction. Cyber ransom and ransomware attacks have been the most popular forms of cyberattacks as of late.
Cyber Ransom
The most common form of cyber ransom is through a distributed denial of service (DDoS) attack. In a DDoS attack, hackers flood a business’ site with data requests, overwhelming the site’s legitimate functions. The flooding eventually forces that website to shut down. As far as the ransom is concerned, cybercriminals will threaten to launch an attack on an organization’s site unless the organization pays a ransom fee of a certain Bitcoin amount.
Another form of cyber ransom is through corporate extortion which is becoming more and more popular. This type of attack can be carried out in several ways. One approach, which Domino’s in Europe was hit with, is where a cybercriminal sends out a ransom letter threatening businesses with negative online reviews, complaints to the Better Business Bureau, harassing telephone calls, or fraudulent delivery orders.
Another variation of corporate extortion is where cybercriminals perform a data breach, where they gain access to a company’s network and gather sensitive data. The data collected is usually information on their clients such as credit cards, social security numbers, email addresses, and login credentials. While this seems like data breaches that we have heard about recently (Yahoo, Adult Friend Finder, and several social media sites), cybercriminals who are involved in corporate extortion are in it for the money. Once cybercriminals have performed the data breach, they will threaten to publicly release the information unless the company pays a set ransom fee.
Ransomware
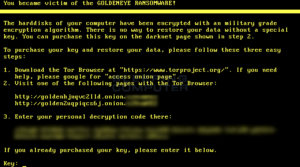
Ransomware is the most common form of cyberattack seen today. In a ransomware attack, the cybercriminal will infect a machine with malware that encrypts all or some files on a user’s computer. Once the encryption process has completed, a ransom note will appear on the victim’s screen demanding payment in order to receive the decryption key. Payment for the decryption key is usually made in Bitcoins, which are extremely hard to trace back to the hacker. Ransomware is most commonly distributed through phishing campaigns where cybercriminals will send emails embedded with malware. Once the user on the receiving end clicks on a link or opens up an attached file, the malware will begin to download, and the encryption process will begin.
Cyber Ransom and Ransomware Connected
- Cyber Ransom – Cybercriminals threaten to launch a DDoS attack on an organization’s site unless the organization pays a ransom fee.
- Ransomware – Cybercriminals infect machines with malware that encrypts all or some files, then demand a ransom fee to receive the decryption key.







 were the case, those of us in the cybersecurity industry would be without employment. However, training to reduce the risk of cybercriminal activity is essential to a company’s bottom line. Without training and security measures we may as well leave the front door open at night with a sign stating, “Welcome all criminals.”
were the case, those of us in the cybersecurity industry would be without employment. However, training to reduce the risk of cybercriminal activity is essential to a company’s bottom line. Without training and security measures we may as well leave the front door open at night with a sign stating, “Welcome all criminals.”