
Ransomware:
Ransomware is a kind of malware that encrypts everything on your system with a Cryptographic algorithm and holds that encrypted data hostage for ransom. It demands the user to pay for the decryption key. There are two types of ransomwares. In first, ransomware encrypts all data on the system and it is nearly impossible to decrypt it without the key. In second, it simply locks the system and demands to enter the key for data decryption but it does not encrypt data.
One of the very well-known ransomware is Cryptolocker. It uses RSA to encrypt data. Command and control server of malware stores the private key for decryption of data. It typically propagates as a Trojan and it relies mainly on social engineering for propagation.
Working of ransomware (unlike its purpose) is quite interesting. For proper understanding, we can divide its working in following steps.
- Approaching system of the victim and installing it as a covert/silent installation. It places its keys in system registry.
- After installation, it contacts its command and control center. The server tells the ransomware what to do. It starts communication by performing handshake with the server and exchange keys.
- Now it actually starts working, with the key provided by the server it starts encrypting the data on the machine. It uses common file extensions to identify the files and encrypt them.
- This is where it gets scary. After encrypting the data, it shows a message on screen that it has locked data on your computer and you have to pay within a period if you want to see your data again.
How it propagates:
Ransomware mostly uses social engineering tricks to propagate. It uses email attachments with malicious files and covert or maliciously forged documents with embedded scripts. In addition, it uses malicious URLs that point to vulnerable and compromised sites. Internet surfing and downloading software with unknown publishers is also a likely reason of infection. Ransomware also spreads through mediums like USB, portable hard drives etc.
Ransomware installation:
Its installation is a covert operation. It uses Windows default behavior to hide the extensions from name of the file, disguising the real .exe extension. Once it reaches its target by using any of the above mentioned propagation methods and user opens the malicious file, it becomes a memory resident on the computer. Then it usually saves itself in the Appdata folder, User Temp and Localappdata folders. Later, it adds a registry key in the windows registry to start the malware every time windows restart.
Main working:
The main purpose of ransomware is encryption of data on the target computer. It generates a random symmetric encryption key for each file. It targets files with general extensions like .jpg, .doc, .docx, .xls, .png, .ppt, .pptx, .jpeg etc. and other files whose extension are in the malware code. It uses AES algorithm to encrypt data files. After encrypting data, it encrypts a random key with asymmetric private key using RSA algorithm and adds this to encrypted file. Now only the owner of the private key can have access to the random key it generated to encrypt the data.
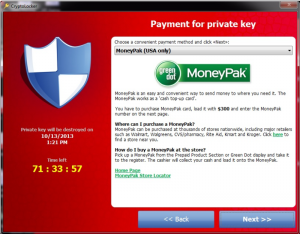
The malware communicates with its command and control center to obtain the public key. It uses Domain generation algorithm (DGA) with common name as “Mersenne Twister” to generate random domain names and find its command and control center. After encrypting data, it displays a message with the time limit to the user about the ransom that has to be paid for the key and failed to do so will delete the key.
The compromise system can have the symptoms like high rate of Peer to Peer communication, increased network communication (Communication with Command & Control center server) and high use of system resources.
Mitigation and Prevention:
So far, there is no way that can break the Cryptolocker encryption and provide you the key to decrypt data. Paying seems to be the only way to get data back unless you have a backup. Some of the incidents in past showed that paying did not pay back. As some people paid but did not get the key and in other cases the given key did not work. So the best way is to keep yourself save proactively. Now we are going to discuss some proactive approaches to keep yourself safe from these types of attacks, in case you are affected what steps to take.
- The first and the foremost thing that comes into play when we talk about security is User Awareness. Training of the employees, users and all stakeholders is the most important thing. As in this case, we are in a war against malware. In addition, users cannot win this fight unless they are aware of the threats. SOC/Security management team can organize seminar, awareness campaigns etc., to guide the employees. Periodic briefing is also important. Explaining the cases with examples to the non-technical as well as technical employees can make it better for them to understand and remember the scenarios they are likely to face in everyday life.
- Along with user awareness, implementation of security policies is inside the domain via GPO and email transport rules to block such potential type of emails and Exes to execute silently. One recommends it highly to use Security Group policies in your organization for safeguarding against malware. Let us walk through the process of implementing the same.
Certain application and programs apply software restriction policies for their execution. This uses Group policy. What we can do is to block the executable in the specific user space areas where the ransomware launches itself. In large organizations, we can do this via Domain Group policies. In small business environment, home or organizations with no domains apply local security policies.
- Open Group Policy management console on your primary DC to implement a Software restriction policy.

- Create a New GPO. Name it as “Software Restriction Policy”.
Well the folder structure for users in Windows XP and prior is a bit different so what we can do is, to create 2 different policies; one for XP systems in domain and other for Vista and higher version of OSs. What I would do is, I will add both types of folders for XP and later in one GPO.


- Now edit the newly made GPO and add user space folders in which we don’t want the software to auto execute. Go to Computer Configuration> Policies > Windows Settings > Security Settings Software Restriction Policies > Additional Rules. Right click Additional Rule and click ‘Add new Path rule’. Here we will create a new rule and enforce software restriction.

- We will be adding file paths here. Add a path, select security level ‘Disallowed’ and add a description.
The paths for XP user space are as follows:
- %AppData%\*.exe
- %AppData%\*\*.exe
- %UserProfile%\Local Settings\Temp\Rar*\*.exe
- %UserProfile%\Local Settings\Temp\wz*\*.exe
- %UserProfile%\Local Settings\Temp\*.zip\*.exe
- %UserProfile%\Local Settings\Temp\Rar*\*.exe
The paths for other higher version of OS are:
- %LocalAppData%\Temp\*.zip\*.exe
- %LocalAppData%\Temp\7z*\*.exe
- %LocalAppData%\Temp\wz*\*.exe
- %LocalAppData%\Temp\Rar*\*.exe


- Now allow sometime to let the GP sync to all the systems or you can go to every system and open cmd as Administrator write ‘gpupdate /force’ to force update the group policy to the system and now you are done.
There can be a disadvantage of applying the software restriction policy i.e. all the other legitimate exes will not run in those spaces as well. However, we can whitelist the legitimate software in Software Restriction policies.
For Whitelisting apps in Software Restriction policy, exceptions have to be set for those apps. We can manually instruct windows to allow those apps while block all the others. For doing so just add same rule for particular apps as explained before and set security level to Unrestricted instead of Disallowed. This will allow the GPO to whitelist the apps and their execution takes place in user space.
- If you have on-premises email server or exchange, Transport rules are something very useful. Use the exchange transport rule to block or disallow attachments with executable content or at least mark it as Possible Spam so User may have warned by the content of the email.
- Open Exchange Management Console on your exchange server.
- Go to Organization Configuration > Hub Transport.
- Open Transport Rules.

- Add new rule by right clicking the main screen. Enter the Name of the rule along with the description of rule.

- Select the condition for the rule from next window. Select option “When any attachment file name matches text patterns”.

- Select as much extensions as you want. Here we are adding exe, html, doc, docx, jpg, jpeg, zip, rar etc.
- Select the Action that the rule will perform after meeting the conditions. Select the option “prepend message subject with string”. Now add “Possible Spam” as the text that will be added in the subject line.

- If there are any exceptions, add them on the next screen else left it as it is. Complete the process by click Next and then Finish. The transport rule is added and its enable with priority set to 0.

Now when the user will receive the email with those specific extensions that we added in rule, he will observer Possible Spam in the subject of those emails.
3. User permissions: It is something minor but very important when we are dealing with the threats like ransomware. Review the NTFS permissions carefully for every time we deal with permissions. For instance, Share folders from server etc. If the share folder has ‘Everyone’ write permission and the user system gets infected, you are in trouble. Try to give the as minimum permissions as possible to users to lessen the damage.
4. By this time, many antivirus softwares are able to detect and remove this virus but decryption of the data is not possible unless you have the key. Keep your antivirus updated so it can detect and remove the malware before it acts.
5. Keep your systems up-to-date and patched up with latest security patches that the manufacturer releases.
6. Do not allow Peer to Peer communication in your network. Ransomware and many of the other malware and bots communicate with their command and control center via P2P communication. Disallowing this will help you keep save.
7. Use Security devices like firewalls and IDS/IPS in your network and configure them appropriately and intelligently.
8. Avoid using such type of unknown anti-virus on your system even if it claims to remove the malware from your network or system. Ransomware encryption cannot be broken easily and data cannot be decrypted without a key so if any unknown anti-virus claims that it can break encryption in no time don’t get tricked. It is some other type of malicious virus.
9. Last but not the least: Rather it is the most useful solution I know so far, is to BACKUP all your data regularly. I have seen clients affected with ransomwares and the only thing that saved them was Successful backup. Backup all your critical data to the external drive or NAS or SAN that is isolated from your system is very useful. If you are a big organization, then develop a BCP (Business Continuity Plan) and BDR (Backup and Disaster Recovery). BCP contains all the aspects of ransomware attacks and migration techniques along with the details of the backup you can or will take for your organization. There are many backup solutions available in the market that can help you backing up your data to an external storage or remote location i.e. cloud storage.
Thank you Tal for the great Post:
Tal Eliyahu
Operational Security Specialist | OSCP, CREST, ISO 27001, 22301 & 22035 Certified Lead Auditor and 27005 Risk Manager






















