One huge mistake people make when renting cars
There are plenty of reasons to rent a car, from leaving a less reliable or gas-guzzling car behind on a long trip to getting around a city on a business trip or while your car is being repaired. It’s not necessarily cheap, but if you need to move around a lot, or go any substantial distance, it isn’t any worse than taking a cab or calling for an Uber, and it might be more convenient.
Is your company leadership connecting to rental cars with company phones and leaving text messages, contacts, call logs? Is there deal information or IP in those text messages?
There is a hidden danger, though, that not a lot of people realize. Rental companies upgrade their fleets regularly with newer-model cars, which means your rental has new technology, including a high-tech infotainment system. That’s not the bad part.
Newer infotainment systems let you pair up your smartphone via Bluetooth so you can take calls over the car’s audio system, dial from the center console or stream your music. Others include USB so you can get everything I just mentioned and charge your phone at the same time.
That’s also not the bad part, as long as you own the car. When you’re renting, however, it can be a danger.
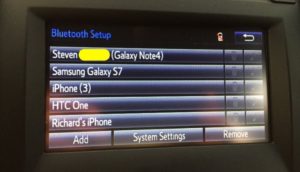
When you connect up to a car with Bluetooth, the car stores your phone number to make it easier to connect later. It also stores your call logs, and possibly even your contacts. This isn’t something you want sitting around for the next renter.
Go into the settings (it will vary for every car model) and delete your smartphone from the list of previously paired Bluetooth gadgets. That should wipe your call log and contacts as well. If it doesn’t, look for an option to clear user data or do a factory reset. Talk to the employees at the car rental place if you can’t find these options. Like any hard drive, you can possibly still recover data after it is wiped.
If you used the car’s navigation system to get around, be sure to go in and clear your location history. You don’t want the next person knowing where you’ve gone, or where you live. If you own the car and are selling it, you’ll want to do this kind of wiping as well.
Aside from privacy concerns, there’s a security concern, too. We now know that cars can be hacked, and as they get more advanced the chance that a car can get infected with a virus increases. If the car’s system was compromised by a hacker or previous renter, hooking up your phone would give a hacker access to everything on it.
The obvious solution is to not pair your phone with the car’s systems at all. If you want to listen to music, use an auxiliary cable to connect the headphone port on your phone to the audio system directly. For charging, use the cigarette lighter instead of the USB port.
If you want to do hands-free calling, you can purchase a third-party Bluetooth audio kit that does the job. It’s also great for adding this feature to an older car with a less advanced infotainment system.
Hopefully, the privacy concern with car infotainment systems should be going away in the future as Android Auto, Apple CarPlay and similar systems become standard on more cars. These systems don’t store any information, they just read it off your smartphone. So when you take your smartphone out of the car, none of your information stays.
Of course, it will be years or even decades until cars with less secure infotainment systems are off the market or no longer in used car lots. And you never know what other systems will come out in the future and how secure they’ll be.
Please share this information with everyone.

