Social Security numbers, birth dates, addresses and driver’s license numbers exposed.

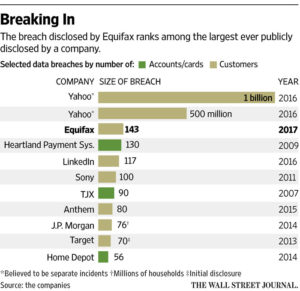
Credit-reporting company Equifax Inc. said Thursday that hackers gained access to some of its systems, potentially compromising the personal information of roughly 143 million U.S. consumers in one of the biggest and most threatening data breaches of recent years.
The size of the hack is second only to the pair of attacks on Yahoo disclosed last year that affected the information of as many as 1.5 billion customers. It also involves nearly twice the number affected by one of the highest-profile breaches at a financial firm, the cyberattack at J.P. Morgan Chase & Co. about three years ago.
The Equifax breach could prove especially damaging given the gateway role credit-reporting companies play in helping to determine which consumers gain access to financing and how much of it is made available. The attack differs, too, in that the attackers in one swoop gained access to several pieces of consumers’ information that could make it easier for the attackers to try to commit fraud.
Equifax said hackers gained access to systems containing customers’ names, Social Security numbers, birth dates and addresses. The company also offers credit-monitoring and identity-theft protection products to guard consumers’ personal information.
“This is the nightmare scenario—all four pieces of information in one place,” said John Ulzheimer, a credit specialist and former manager at Equifax.
On Friday, shares of Equifax fell 14% to $123.03 in morning trading in New York.
The incident comes at a time of heightened sensitivity to cyberattacks in the political, commercial and personal realms, especially in the wake of presumed Russian interference in the U.S. presidential election last year.
The number of large hacks has increased in recent years—with incidents involving tens of millions of accounts each involving tech companies, banks, retailers and others.
More companies are putting more information online from more users, creating bigger targets for hackers who continually develop and refine their techniques and tools.
Equifax is one of the big three credit-reporting firms in the U.S. and maintains credit reports on more than 200 million U.S. adults. The other two are TransUnion and Experian. Credit reports compiled by such companies include personally identifiable information as well as records of the credit cards and loans consumers have, their spending limits on cards, and whether they are on time with their debt payments.
“This is clearly a disappointing event for our company, and one that strikes at the heart of who we are and what we do,” Equifax Chief Executive Richard Smith said in prepared remarks. “I apologize to consumers and our business customers for the concern and frustration this causes.”
The four pieces of information exposed in the attack are generally needed for consumers to apply for many forms of consumer credit, including credit cards and personal loans. That means that swindlers who have access to this data could have an easier time getting approved for credit in other people’s names and potentially makes it more difficult for lenders to spot a problem. In addition, Equifax said the hackers gained access to some driver’s license numbers.
An added concern is that the breach raises the chances of more fraudulent loan approvals occurring when various forms of fraud are already hitting lenders and contributing to higher losses.
Smaller financial institutions, including community banks, credit unions and online personal-loan lenders, are more vulnerable to the effects of this breach, said Al Pascual, head of fraud and security at Javelin Strategy & Research.
That is because they are more reliant on the four, key pieces of borrower information when determining whether they are dealing with a legitimate applicant, he said. The biggest banks, he added, have in recent years moved to relying on additional information. With online applications, for example, that includes pinpointing what geographic area the applicant is located in to figure out whether they are an actual person or a fraudster.
Equifax said in its statement that while the incident potentially affected approximately 143 million U.S. consumers, “the company has found no evidence of unauthorized activity on Equifax’s core consumer or commercial credit reporting databases.
Equifax said an internal investigation revealed hackers exploited a vulnerability in a U.S. website application to gain unauthorized access to files from mid-May through July. The company said it discovered the breach on July 29.
Equifax said it reported the intrusion to law enforcement and contracted a cybersecurity firm to conduct a forensic review. In the days following the company’s discovery of the breach, three top Equifax executives, including Chief Financial Officer John Gamble, sold shares worth a combined $1.8 million, according to Securities and Exchange Commission filings. A company spokesman said the three executives who sold a small percentage of their Equifax shares on Tuesday, Aug. 1, and Wednesday, Aug. 2, had no knowledge that an intrusion had occurred at the time they sold their shares.
Equifax also said credit-card numbers for approximately 209,000 U.S. consumers were accessed, as well as dispute documents with sensitive information for another 182,000 people.
With the Equifax attack, banks now will have to reissue cards for the approximately 209,000 credit cards stolen in the breach, but for consumers the theft uniquely identifying information such as Social Security numbers and birth dates could have a permanent effect. Additionally, a limited number of people in Canada and the U.K. were affected, the company said.
Stock of other financial companies weren’t initially affected with shares of credit-card issuers and big banks mostly unchanged or up slightly in after-hours trading.
Equifax said it has set up a website—www.equifaxsecurity2017.com—to help consumers determine if their information has been compromised and to allow them to sign up for a complimentary slate of credit-monitoring and identity-theft protection. The company also has established a dedicated call center for consumers.
This is becoming an everyday occurrence. When are we going to get the message to tighten up security across this nation !!


 agreed, saying that he views “IoT as Internet of Threats, not Internet of Things,” and recommended this view as apartment firms evaluate smart home technology. Kevin Gerber, project manager at Forest City Enterprises, noted that it is critical to educate staff on the new technologies and maintaining strong security protocols, and highlighted the need for a strong support structure.
agreed, saying that he views “IoT as Internet of Threats, not Internet of Things,” and recommended this view as apartment firms evaluate smart home technology. Kevin Gerber, project manager at Forest City Enterprises, noted that it is critical to educate staff on the new technologies and maintaining strong security protocols, and highlighted the need for a strong support structure. threats. Best practices for strong cyber hygiene aren’t new. Right now, the onus is on the end-user to ask right questions and educate him or herself until market correction forces vendors pushes vendors to address security.” NIST provides best practices and a customizable approach to managing cyber risk through the NIST Cybersecurity Framework.
threats. Best practices for strong cyber hygiene aren’t new. Right now, the onus is on the end-user to ask right questions and educate him or herself until market correction forces vendors pushes vendors to address security.” NIST provides best practices and a customizable approach to managing cyber risk through the NIST Cybersecurity Framework.












