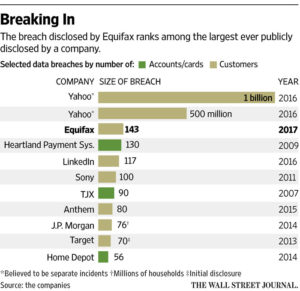
With the Target example as the high-water mark, enterprises need to worry about the lack of security on the part of third-party providers that have access to internal systems.
Most businesses hire third-party providers to fill in when they lack in-house resources. It is often necessary to allow third-party vendors access to their network. But after Target’s network was breached a few years ago because of an HVAC vendor’s lack of security, the focus continues to be on how to allow third parties access to the network without creating a security hole.
The use of third-party providers is widespread, as are breaches associated with them. Identity risk and lifestyle solution provider SecZetta claims that on average, 40 percent of the workforce make up third parties. A recent survey done by Soha Systems notes that 63 percent of all data breaches can be attributed to a third party. “The increased reliance on third-party employees, coupled with the growing sophistication of hackers, has led to the current identity and access management crisis that most businesses are faced with today — whether they realize it or not,” a SecZetta blog post stated.
Rick Caccia, CMO at Exabeam, explained that the Target breach shined a light on the risks that come with trusted partners. On one hand, they often have access to the most sensitive data and systems within a firm’s environment. On the other, the firm has little insight into the partner’s own security processes and doesn’t really know the partner’s employees or their routines.
David Baker, vice president of operations at Bugcrowd, said “The rule of thumb most CSOs live by is that you only use a third party if they do something better than you. So whether that’s delivering a package or managing your data center, if an outsourced third party does it better, it makes sense to use them. This extends to security.”
For example, a large number of organizations have outsourced their data centers to Amazon Web Services (AWS) not only because the functionality of building the technology on AWS is better than what organizations can achieve on their own, but also because the security offered is better than what companies can build themselves, he said.
“If you use a third party and want to avoid something like what happened with Target, you need to have a process by which you select those third parties, and a big part of that criteria should be security. Security has to be something you can measure that they do better than you,” Baker said.
Markus Jakobsson, chief scientist at Agari, said the one big disadvantage to working with third-party vendors is the loss of control over security. “Not only does each vendor create a new entry point into an organization’s network for cyber criminals to exploit, but it also means every employee for that vendor is now a potential target to breach your brand. Unfortunately, the only way to ensure your company is not exposed to greater risks is by keeping everything in-house. But in today’s digital world, this isn’t a reality.”
Mike McKee, CEO of ObserveIT, said the lack of visibility into what users at third-party providers are doing – accidentally or intentionally – is a huge security risk.
“Every organization must ensure it has identified the outside parties with access to systems and data and have secure procedures in place, strict policies for these users to follow, and effective technology in place to monitor and detect if the third parties are putting their organization at risk,” he said.
It is the cost of doing business that leaves your network vulnerable to third parties, said Yitzhak (Itzik) Vager, vice president of cyber product management and business development at Verint Systems. Manufacturers connect directly to suppliers to manage just-in-time production. Accounting departments connect to external invoicing and receipt systems, and the marketing team has given all types of automated solutions access to the network infrastructure.
“Organizations need to assume that they have been already breached by a third-party leaving a hole in your network, and therefore they need to move to detection and response area solutions that consider the big picture, delivering complete visibility by detecting across the entire network, endpoints and payloads.”
Richard Henderson, Global Security Strategist at Absolute, agrees. ”In the majority of cases, companies will have no way to learn if those partners have a breach or fall prey to attack. Add to this that regulators (and customers) really don’t care if someone else was responsible and it seems like an unwinnable battle. After the damage is done, organizations are left picking up the pieces and will be the ones called to task and held accountable.”
Carl Herberger, vice president of security solutions at Radware, said that business units are under a lot of pressure to leverage new solutions to speed time-to-market and reduce costs. Typically, security is a secondary consideration.
“Most of these business teams don’t have the skills or knowledge to assess security requirements and can result in partnering with a vendor who may leave the company’s networks open to attack,” Herberger said.
If an enterprise lets a third party onto their network, regardless of the reason, that third party then becomes an integral part of their security perimeter, notes Amir Jerbi, CTO of container security company Aqua Security. “Organizations should therefore vet third parties for their security measures and practices and ensure they are aligned with their own, and furthermore, periodically check and test those practices to verify they are still in compliance. These checks may (and should) cover systems, process and people.”
Alertsec’s CEO Ebba Blitz advises to make sure everyone plays by your rules. If full disk encryption is mandated for your own staff, make sure that your third parties do the same. “All too many third parties log into your network from unknown devices – devices that you don’t manage and can’t control, unless they are enrolled in your network. Make sure data only flows to encrypted devices, whether they are enrolled in your IT infrastructure or not.”
Third-party risk management
The market has pushed forward with third-party risk management programs to answer this dilemma. A program such as this would tell if a third party was located offshore or onshore, use a corporate issued device or a personal device, have had a background check performed, and whether they will be performing a critical function for the organization.
“When it comes to the cyber world, vendors must demonstrate that they understand security and have a mature security program in place, including policies and employee training,” noted Asher DeMetz, manager- security consulting at Sungard Availability Services. Any third-party systems connected to the company’s network would need to have a proper business function and owner, and align to the company’s own security program (secure, monitored, controlled).
“The software or hardware would need to be validated with the correct security controls and attestation of security testing, and possibly compliance. If the third party is making configuration changes, these would have to go through proper change-management channels to ensure that they align to the security program and don’t introduce risk into the environment,” DeMetz added.
Risk management involving external actors can be a very challenging activity for a variety of reasons, said Bluelock Director of Engineering Derek Brost. “There are two major factors for consideration. First, is sufficiently involving legal counsel to ensure contractual designation of responsibility, diligence and due care. As a backstop, this should also permit enforcement or litigation related to reclaiming loss or damage if things go awry. Second, is allocating continuous resources for proper control and oversight of external activities in the form of authentication management, timely activity analysis, and especially audit review.”
Unfortunately, businesses commonly involve third parties for cost reduction or “quick fixes,” so an adequate level of investment may not be considered in the budget or overall cost for administering external actors, said Brost. However, like all risk management activities, these costs need to be considered up-front as part of the overall tolerance and loss potential.
Kennet Westby, president and co-founder of Coalfire, said every organization should have a robust third-party vendor management program that is built to support the validation that critical vendors are delivering on their committed services. Part of that vendor management process should be to validate that your vendor has internal security controls. If your vendor management program requires these third parties to operate at an even greater standard than your internal controls, you can actually reduce risk more than if internally managed.
That brings us to identity access management. As SecZetta explained in a blog post, no person or department is in charge of managing non-employee identities (people data) and their relationships at most companies. IT might provide access, but the initial access and managing of non-employee changes is charged to HR or procurement.
This is a challenge, especially in cases where non-employees have greater access to sensitive information than internal employees. If a non-employee is granted access to these sensitive systems for a nine-month period but finishes the job early after six months, there are three months in which the non-employee may still have access to sensitive systems. These are exactly the types of accounts that hackers look for when trying to penetrate systems and steal data, according to SecZetta.
Ryan Stolte, co-founder and CTO at Bay Dynamics, said keeping track of who is doing what is a daunting task. “Instead of trying to boil the ocean, keeping tabs on every user for every vendor, security teams must hone in on those that access the company’s most valued applications and systems.”
Instead of trying to boil the ocean, keeping tabs on every user for every vendor, security teams must hone in on those that access the company’s most valued applications and systems.
Ryan Stolte, co-founder and CTO at Bay Dynamics
Effective vendor risk management begins with identifying your crown jewels and the impact to your organization if those crown jewels were compromised, he said. Then, look at which vendors have access to those crown jewels and continuously monitor not just the vendor users’ activity, but also their team members and fellow users in the larger group. If your security tools flag an unusual behavior coming from a vendor user, it’s important to engage the application owner who governs the application at risk, asking the owner to qualify if the behavior is unusual or business justified. If the behavior is unusual, that threat alert should go to the top of the investigation pile.
“It’s important to consider that often third-party vendors are non-malicious threats. Oftentimes, vendor employees are less conscious than full-time employees of good cyber security hygiene and therefore unintentionally expose your company to risk,” he said.
Viewpost’s CSO Chris Pierson said that having a well-developed vendor assurance program is necessary to oversee, quantify, communicate and mitigate risks. This program should consider the company mission, goals and objectives for the vendor, and provide a review process that looks at all types of risk – cybersecurity, privacy, regulatory/legal, financial, operational and reputational.
All vendor risks should then be scored, owned by the business line executive responsible for the product/service, and depending on level of harm, socialized and even approved by a governance risk committee. “By rating your vendors based on the criticality of the product/service they provide and the risks, the company can more adequately manage these risks, request mitigating controls, or off-board the vendor,” said Pierson.
Rod Murchison, vice president of product management at CrowdStrike, said when it comes to security, being knowledgeable after an event happens is insufficient. “Real-time visibility into the security posture of your network is something every organization should strive to achieve and maintain going forward,” he said.
To mitigate these types of threats, the most sophisticated endpoint security solutions can sense and analyze enough data in real-time to ensure that breaches and intrusions are observed in real-time, he added. “These new solutions leverage advancements in machine learning, artificial intelligence and analytics so organizations can quickly observe and fill unintentional, and sometimes intentional, holes left by third-party organizations.”
With the growing landscape of global privacy regulations, such as the General Data Protection Regulation (GDPR), the ability to control the uses of data throughout its life cycle will be critical. Strong access management controls can help, but often data masking and anonymization need to be implemented to manage access to key data fields, said Focal Point Data Risk’s Data Privacy Practice Leader Eric Dieterich.
What’s the solution?
Third-party access requires a layered security approach with dynamic contextual access control applied throughout, said Gerry Gebel, vice president of business development at Axiomatics. For example, one layer of security is to dynamically control who can access your network. Another layer would be to control access to APIs, data and other assets once these third parties are on the network.
Caccia advises that third-party access to assets is a perfect scenario for behavioral analytics, where the system baselines normal behavior of users on the network, even with limited knowledge of who those users actually are. “User behavior analytics (UBA) should be table stakes for any firm that works with partners extensively; it’s the best – perhaps only – way to understand and control what once-removed users are doing on your network and with your data,” he said.
Henderson recommended that companies make sure governance policies around vendor management are bolstered and reinforced. This should include policies around regular and random audits of those vendors. Those audits should have the ability to return quantifiable and definable metrics.
Also when it comes to creating and drafting contracts with these vendors, it’s critical that the appropriate sections clearly define the security and privacy obligations expected of the vendor are included.
“I like the idea of inserting data canaries into the record sets that are shared with third parties and then watching for those canaries to pop up in dumps online. You would be amazed at how often data leaks onto the web and shows up in places like pastebin,” Henderson said. “Other things that make me nervous about this problem are quite simply the fact that all the staff, resources, tools and technologies can often be defeated by nothing more than some middle manager somewhere dumping a huge amount of customer data into a spreadsheet then sending it off via email to some previously unknown third party contracted by a business unit to run a bulk email campaign.”
For other enterprises an important lesson is to ensure that third parties have no way to reach those portions of the network, he advised. “Microsegmentation of your environment, as well as many other tools designed to keep traffic from co-mingling, can stop or at the very least, slow down an attacker, giving your security teams valuable time to detect and respond to an incident,” he said.
While it’s not possible to avoid third parties, Javvad Malik, security advocate at AlienVault, said there are many fundamental security practices that can help mitigate the risks. Examples of such would include:
- Knowing your assets – by understanding your assets, particularly critical ones, it can be easier to determine effectively what systems third parties should have access to and restricting it to those.
- Monitoring controls – having in place effective monitoring to determine whether third parties are only accessing systems they should and in a manner they should. Behavioral monitoring can help in this regard by highlighting where activity falls outside of normal parameters.
- Segregation – by segregating networks and assets, one can contain any breaches to one specific area.
- Assurance – proactively seek out regular assurance that the security controls implemented are working as intended.
Jeremy Koppen, FireEye principal consultant, said there are four security controls that should be discussed regarding third-party access:
- Assign a unique user account to each vendor user to better monitor each account and identify abnormal activity.
- Require two-factor authentication for access to applications and resources that could provide direct or indirect access to the internal network. This protects an organization in case the vendor’s user credentials are compromised.
- Restrict all third-party accounts to only allow access to systems and networks required.
- Disable all accounts within the environment upon termination of third-party relationship.
In the enterprise application development world, Jerbi sees many companies being caught off guard by third-party use of emerging technologies such as virtual containers. If a company is using containerized applications from a third party, that application should be vetted for container-specific security risks such as vulnerabilities in container images, hard–coded secrets and configuration flaws.
Baker said there are plenty of best practices to look for when choosing a vendor: how transparent is their security? Do they have third-party security testing? Do they share the results of that testing? “In the end, choosing a secure vendor alone won’t necessarily prevent another Target, but it will prevent the third-party firms you work with from being the weak link,” he said.